Understanding network traffic is key to security and efficiency. Our solution maps all application flows, providing a clear view to optimize performance and detect vulnerabilities.
Empower your network security governance
audits, evaluates, and enhances your security policies to ensure optimal compliance and robust protection.
WITH DANE'S, APPLICATION NETWORK SECURITY POSTURE MANAGEMENT
We make cybersecurity simpler
Optimizing Your Network Security
Map All Network Flows by Application
Continuously Audit Security Policy
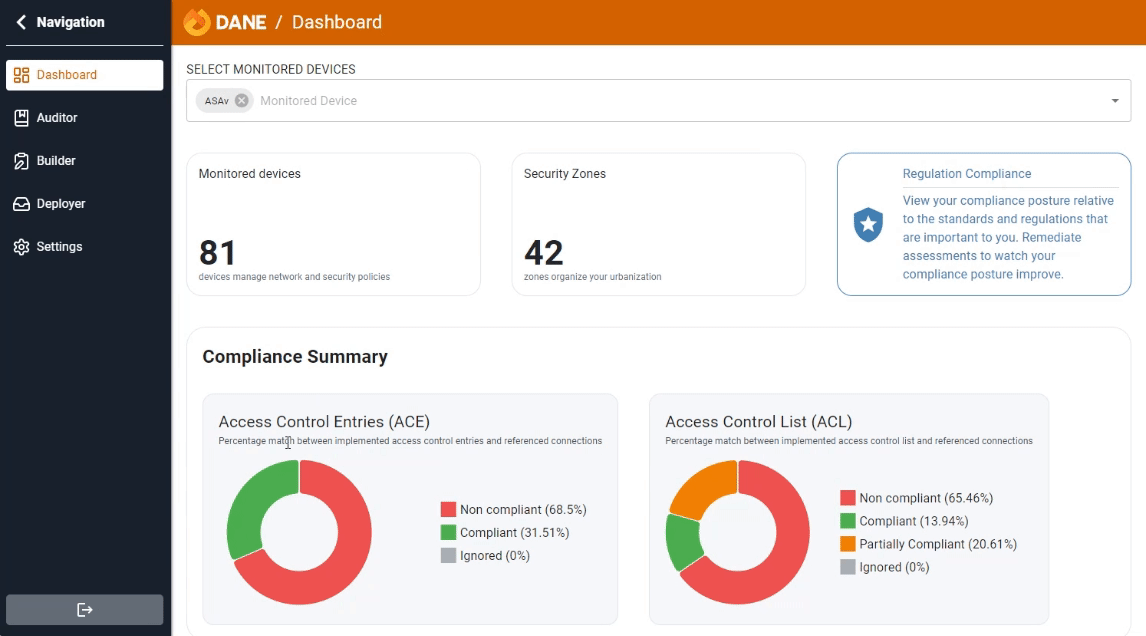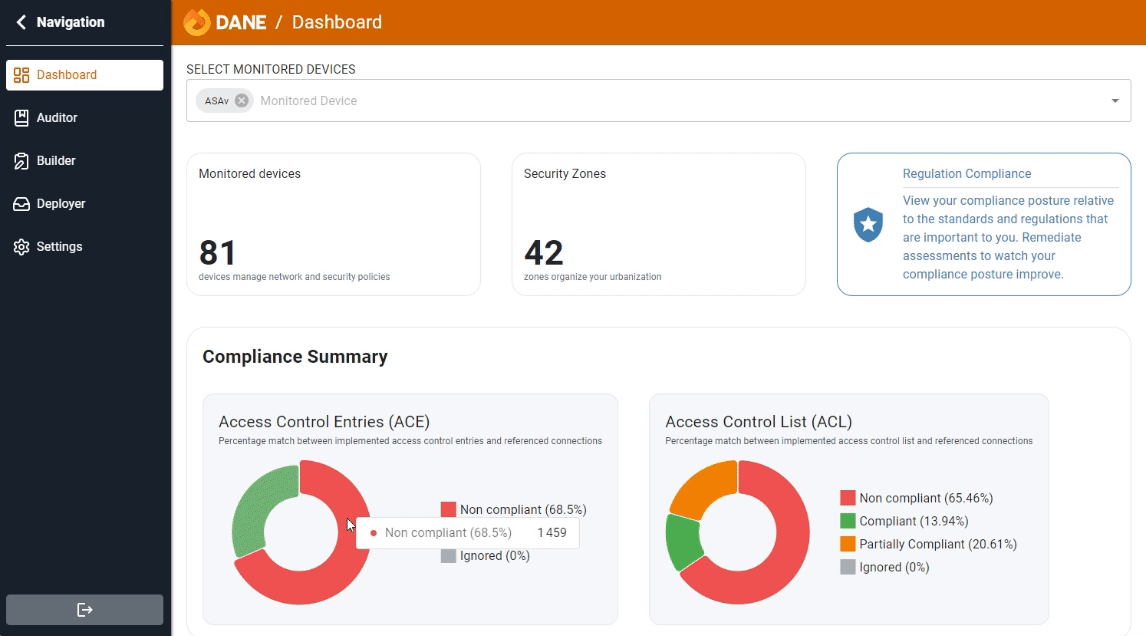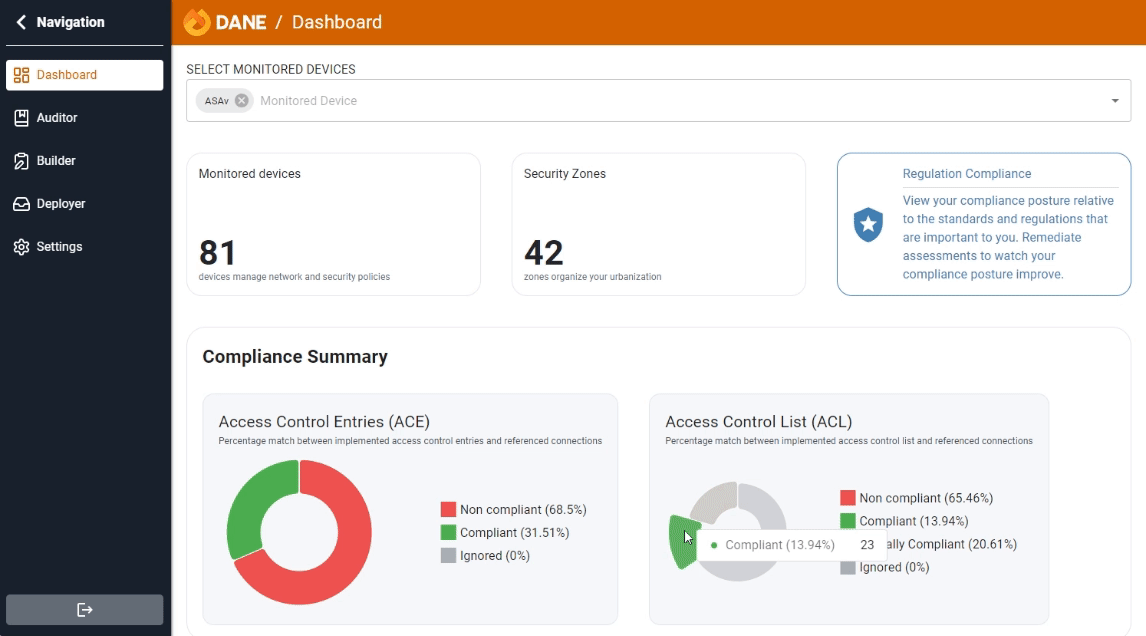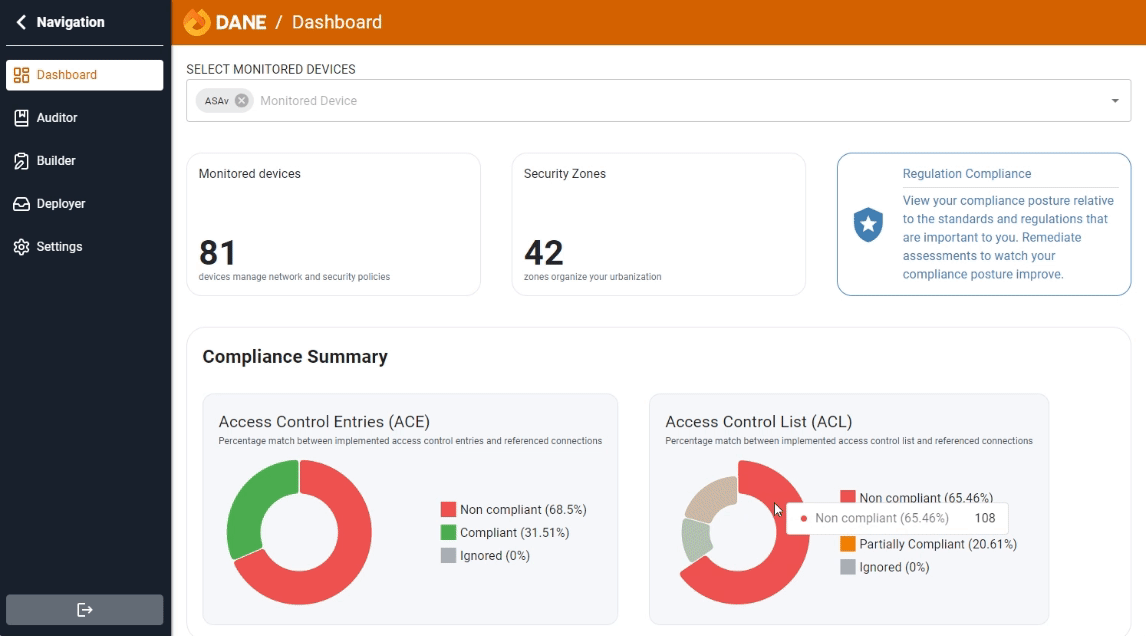
Ensuring compliance is key to network security. Our continuous audit detects and reports policy deviations, helping you stay aligned with standards and enhance security.
Deploy Policy Templates Efficiently
Simplify security with pre-defined templates, ensuring consistency and reducing errors. Deploy standard or custom policies quickly to strengthen your network.
Identify and Close Permissive Rules
Overly permissive firewall rules can create security risks. Our solution identifies and tightens these rules, allowing only authorized traffic and strengthening network defenses.
Secure Your Network with Confidence
Streamline your security policies and safeguard your data with our advanced tools.

Connect seamlessly with our technology integrations!
Our platform adapts to your needs with a dedicated Tufin connector and an abstraction-level universal connector compatible with any REST API.
Key Features to Enhance Your Network Security
Unlock the Full Potential of Your Network Security
From auditing security policies to deploying configuration templates and analyzing network flows, our features keep your network secure, compliant, and efficient. Discover how each key feature can transform your network security strategy.
Builder
Builder allows you to create and maintain comprehensive repositories for all your network applications. This feature ensures that your network’s application data is always up-to-date, providing a solid foundation for managing your network infrastructure efficiently.
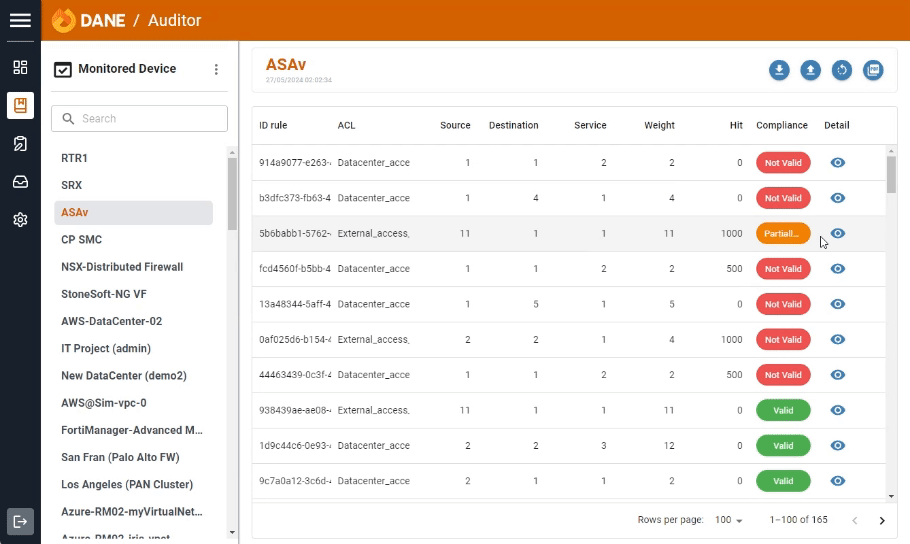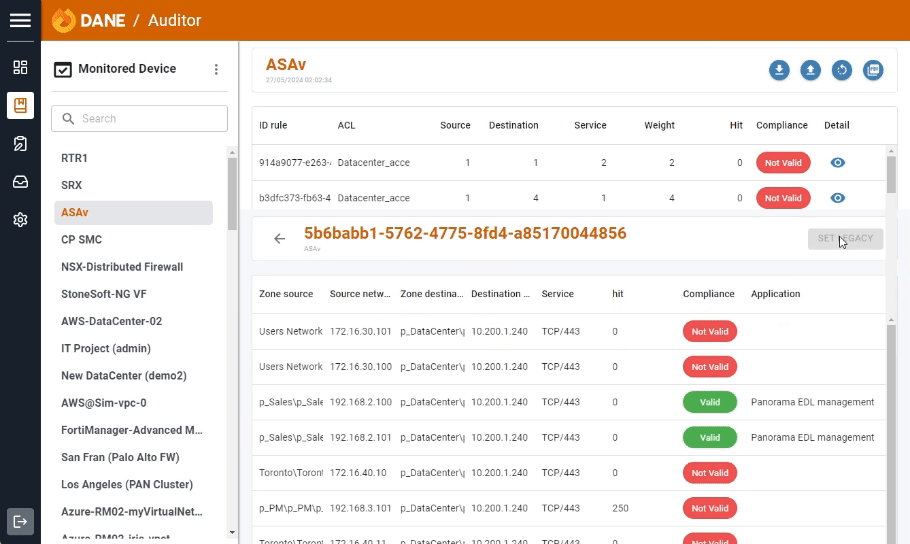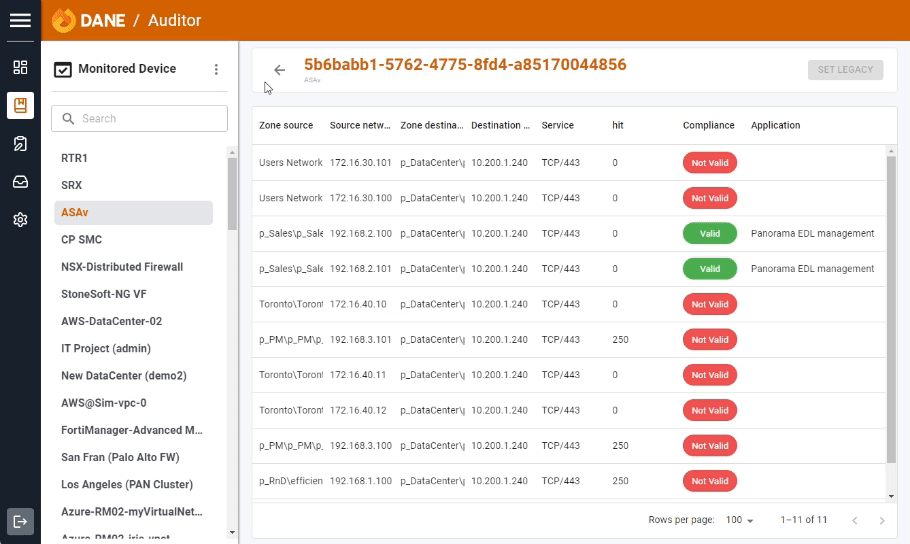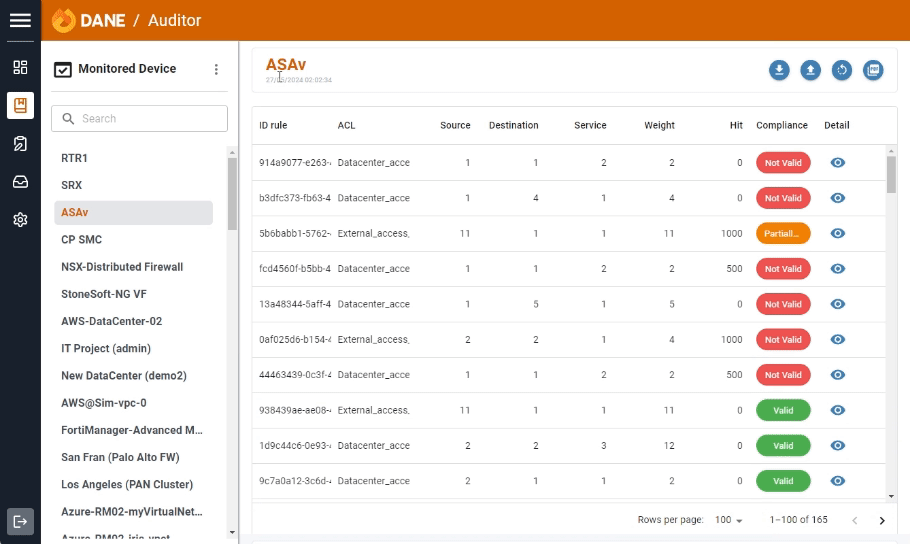
Auditor
Auditor enables you to thoroughly audit your network security policies. By comparing access rules in firewalls against the application repository, Auditor ensures that your security measures are both effective and compliant with organizational standards.
Deployer
Deployer simplifies the process of implementing security policies by allowing you to deploy configuration templates. This feature is particularly useful for addressing permissive security policies, ensuring that your network remains secure and free from unnecessary vulnerabilities.
Why Regular Security Policy Audits Are Essential?
Fortifying Your Network Defenses
Ensure Regulatory Compliance
Compliance with regulatory standards is mandatory for many industries. Auditing your security policies ensures that your organization adheres to relevant laws and regulations, such as GDPR, HIPAA, and PCI-DSS. This not only helps avoid hefty fines but also builds trust with customers and partners.
Reduce the CyberRisk
Effective auditing can significantly reduce the need for third-party security tools. By ensuring that your policies are robust and well-maintained, you can rely more on your internal systems and processes, leading to cost savings and a more streamlined security infrastructure.
Facilitate Network Segmentation of IT Infrastructure
Effective IT system segmentation is crucial for minimizing the impact of potential security incidents. By auditing your security policies, you can ensure that your network is properly segmented, limiting the spread of threats and enhancing overall security.
Accelerate Network Re-Urbanization Projects
Network re-urbanization and segmentation projects require precise and well-documented security policies. Regular audits provide the necessary insights and documentation to support these projects, ensuring that they are executed smoothly and efficiently.
Take the first step towards a more secure network.
Take Control of Your Network Security Today
Ensuring your network security is robust and compliant is more important than ever. Our comprehensive suite of tools and features is designed to help you achieve this with ease and efficiency. From mapping network flows and auditing security policies to deploying templates and hosting application repositories, we provide everything you need to enhance and maintain your network security.


